Secret Management with Loft
Loft allows you to managed shared secrets that can either be retrieved via Loft CLI and kubectl, or they can be instantiated as synchronized Kubernetes secrets in namespaces and virtual clusters.
Working with Shared Secrets
Creating Shared Secrets
Create a Shared Secret
- Go to the Secrets view using the menu on the left
- Click on the button
- Use the Display Name field to define the name of this secret
- Use the Secret Data textarea to add key: value pairs as secret data
- OPTIONAL: Expand the section to configure who can view or edit this secret
- Click on the button at the very bottom
Using Shared Secrets
Retrieve via Loft CLI
To retrieve the value of a shared secret using Loft CLI, run:
loft get secret [secret-name].[data-key]
Use In Kubernetes Secrets
Create a file named
secret.yamlwith content:apiVersion: v1
kind: Secret
metadata:
name: my-secret
labels:
loft.sh/sharedsecret-name: my-shared-secret
loft.sh/sharedsecret-namespace: loft
type: OpaqueCreate the Kubernetes secret using kubectl:
kubectl apply -f secret.yamlShortly after creating the secret, Loft will populate the data of this secret with the data from our shared secret:
kubectl get secret my-secret -o yamlData SyncBy default, Loft will update the data of this secret whenever the shared secret's data is updated. To disable this behavior, set the
loft.sh/disable-sync: trueannotation on the Kubernetes secret.
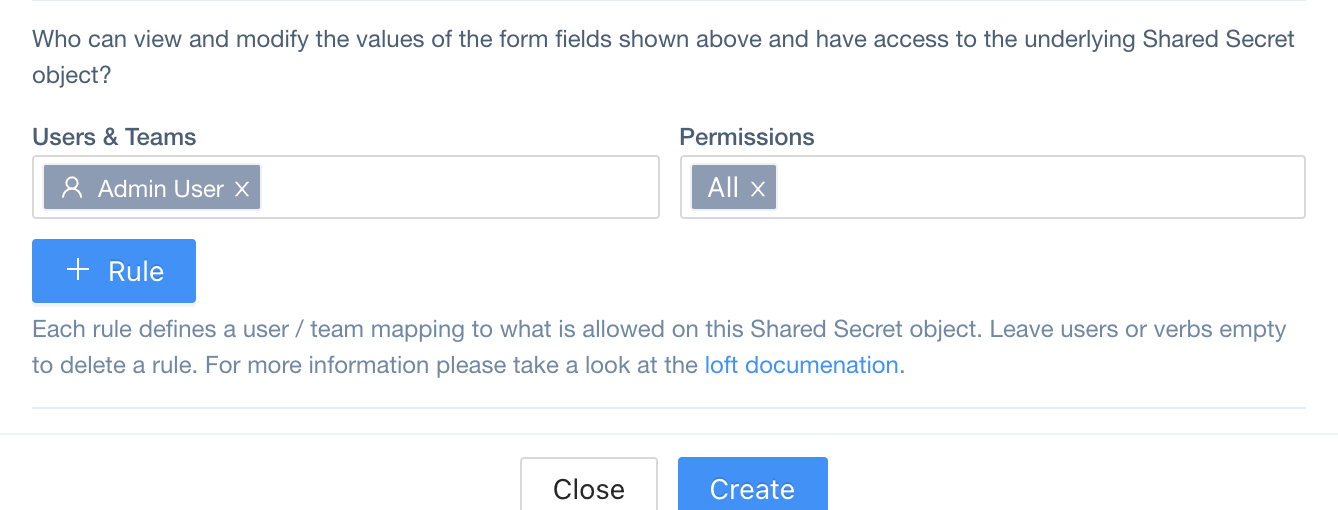
Control Access To Shared Secrets
Configure Access To Shared Secrets
- In the Secrets view, hover over the secret that you want to give someone access to
- While hovering over the row, you will see buttons appear on the right in the Actions column
- Click on the button to Edit the secret
- In the drawer that appears on the right, expand the section
- If the user or team is not listed under Users & Teams yet, click the + Rule button to add another row for a new user or team
- Use the Users & Teams field to select the Users and/or Teams who should get access to this app
- Use the Permissions field to specify if a user is allows to view, update, ... this app definition
- On the very bottom, click on the button to save the changes
Configuration
Metadata
Display Name
JSONPath in SharedSecrets CRD:
spec.displayName (type: string)
Kubernetes Name
JSONPath in SharedSecrets CRD:
metadata.name (type: string)
Description
JSONPath in SharedSecrets CRD:
spec.description (type: string)
Labels

JSONPath in SharedSecrets CRD:
metadata.labels (type: map[string]string)
Annotations

JSONPath in SharedSecrets CRD:
metadata.annotations (type: map[string]string)
Namespace
JSONPath in SharedSecrets CRD:
metadata.namespace (type: string)
Data
JSONPath in SharedSecrets CRD:
spec.data (type: map[string]string)
Access To Secret
JSONPath in SharedSecrets CRD:
spec.access (type: Access[])